Cybersecurity is nowadays a vital component of process control systems (PCS) for maintaining a secure, safe and sustainable control of chemical and energy processes. Unlike traditional IT systems, where endpoints are usually personal computing devices used by people, PCS systems interface directly with the physical components of industrial environments: machines, sensors, and control units. This fundamental difference shapes the nature of potential threats .
The cyber-physical nature of PCS systems means that a breach or failure not only risks data loss but can lead to tangible, often catastrophic, real-world consequences. From halting production lines to compromising water treatment facilities, the ripple effects of these incidents underscore the criticality of robust cybersecurity measures.
The threat landscape consists of:
- Problems with physical endpoints like sensors and motors delivered by 3rd parties which cannot be fultime monitored.
- Direct impact on physical processes.
- 24/7 operation
- Exploitable vulnerabilities: many PCS systems were designed and implemented before cybersecurity became a critical concern, with legacy systems particularly vulnerable due to outdated protocols and lack of encryption.
Only which standard do we have to choose? The norm IEC62443 is a proven and reliable tool for PCS developed by ISA (Istrument Society of America) that is accepted and implemented by many industries all over the world. The NIST, The National Institute of Standards and Technology Cybersecurity Framework, is a voluntary framework primarily intended for critical infrastructure organizations to manage and mitigate cybersecurity risk. The IEC norm will be used as a basis for this paper, additional some extra items as indicated by NIST will be summarized.
Compliance with cybersecurity standards ensures that cybersecurity is an integral part of the company’s lifecycle, and ensures that the necessary measures are implemented to address any shortcomings detected in the implementation process.
IEC 62443, “Industrial communication networks – Network and system security,” provides a critical framework guiding the protection of PCS. This series of standards recognizes the unique requirements of industrial environments and addresses the inherent challenges in securing them. Initially, PCS were not designed with cybersecurity in mind. Their security largely hinged on physical isolation, a concept rapidly becoming infeasible in today’s interconnected world.
For PCS several components can be used which all have comparable vulnerabilities, like:
- PLC, DCS , safety controllers and SIS
- Remote I/O, frequency controllers for E-motors, sensors, barcode readers and RFID readers.
- SCADA, operator terminals, HMI’s and monitors
- Switches, routers, firewalls, wifi accespoints and gateways.
- Surveillance camera’s, entry card readers and badge readers.
The IEC62443 norm consists of the following items:
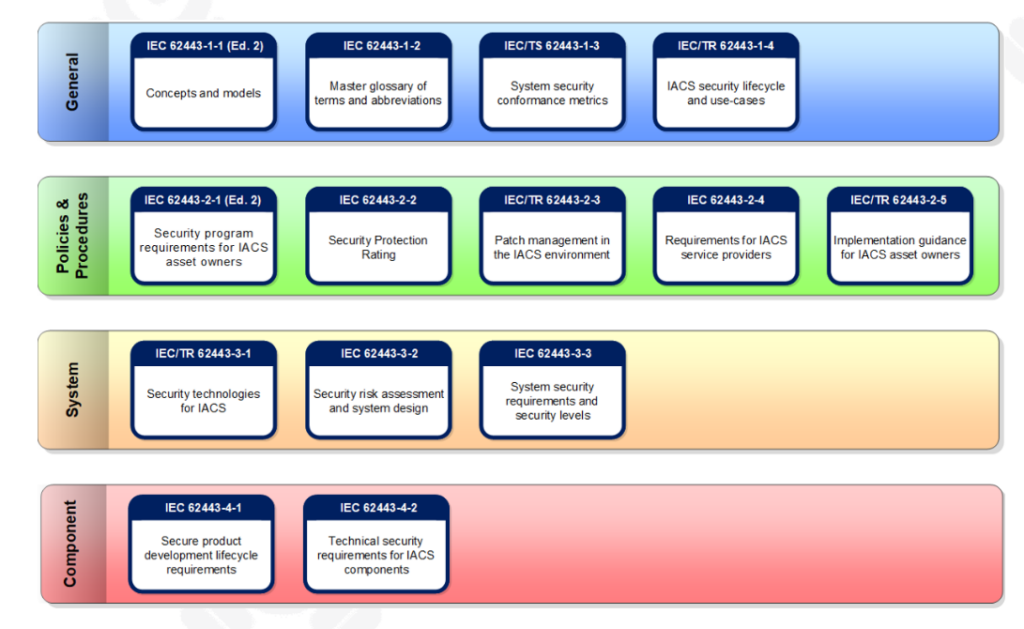
The main objective of control system security is to keep the plant safe and to keep production
running. In contrast, IT security focuses on protecting data, such as credit card numbers, from
being stolen. The primary threat to both of these goals is the infiltration of malicious software into
the system.
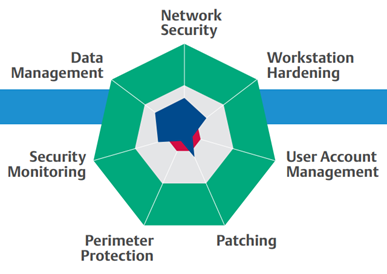
There are six steps that need to be addressed for this threat. They define not only the security mechanisms needed in a control system, but also the supplier capabilities needed to harden the system at the site.
Also make sure that there are security policies for the control system. IT departments all have security policies that can be reviewed if there is not one yet for the PCS. Security policies should support each of the steps below and be geared toward keeping unauthorized software off the PCS.
The six steps make use of levels as defined by NIST (Purdue-model) and (partly) by IEC.
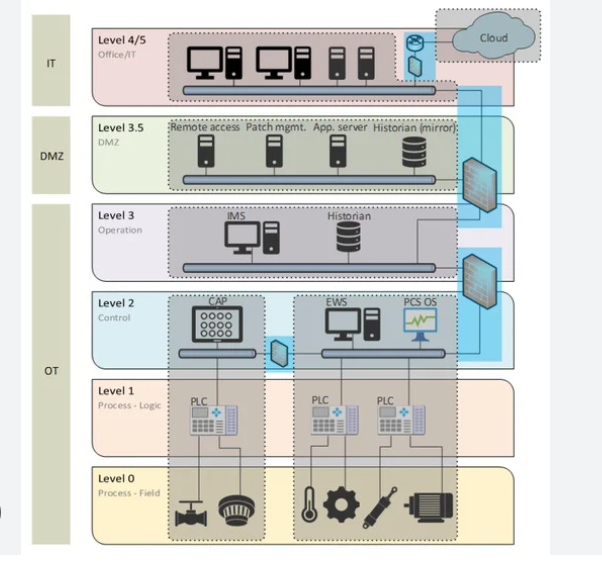
Additionally to this model IEC62433 uses zones and conduits.
Zone: consists of the grouping of cyber assets that share the same cybersecurity requirements
Conduit: consists of the grouping of cyber assets dedicated exclusively to communications, and which share the same cybersecurity requirements
Step 1: Network security perimeters
This involves establishing network security perimeters to restrict access points where foreign
software can enter the automation system. As shown above, in a typical control system plant/enterprise networks are at Level 3 and above in the Purdue model, while the control system networks and buses are at Level 2 and below. Disconnect unnecessary connections to the PCS network. Firewalls are used to segment the control system internally and to isolate it from Level 3 and other external networks. Ensure that all traffic to/from the control system is encrypted and passes through at least one firewall. Further, under no circumstances should any Level 2 workstation be granted direct access to the Internet, or have an IP address that allows it to be directly accessed from the Internet.
Within the control system, firewalls should be used to protect controllers, wireless device
networks, and SIS networks from Level 2 workstations. In addition, switches with lockable ports
should be used to prevent unauthorized devices from connecting to the control system. These
firewalls and switches, in conjunction with the Level 3/Level 2 firewalls, create a layering of
security perimeters with the lowest degree of trust attributed to Level 3 and the highest level
granted to Level 1.
Components that are not critical to safety and availability, such as historians and data servers,
should be installed at an upper level in the hierarchy, with less protection, but correspondingly
more access, so that plant personnel can view data and make changes as needed.
Once the firewalls and smart switches are installed, they must be maintained throughout the
lifetime of the system to keep their effectiveness from degrading. Firewall rules must be kept
current to reject changes to IT and control systems and to protect against newly discovered
threats. Unused switch ports must be regularly checked to make sure they are still locked. Implement the security features provided by device and system vendors.
Step 2: Workstation hardening
This involves hardening control system workstations to make it more difficult for malicious
software to find a way into the system. Five primary hardening activities should be performed.
First, the Center for Internet Security (CIS) hardening template should be applied to lock down
the workstation’s security policies.
Second, these workstations should be dedicated to operator and engineering functions, and, as
such, all applications, services, and ports that are not needed to support these functions should be
removed or disabled to prevent vulnerabilities they may have (known or unknown) from being
exploited.
Third, anti-virus software should be installed to detect and delete known malware before it can
infect the workstation. In addition, virus definition files should be kept up to date to keep up with
new viruses that are circulating. Fourth, the file system should be configured to permit only authorized users to access sensitive files. The default, unfortunately, is to allow users with administrator privileges to access all files on the workstation. These users should be carefully analyzed, and they should be granted access only to files/directories that they need. Fifth, USB, CD, and DVD drives should be locked down when not used for authorized purposes.
Additionally, users should be reminded that using portable media is a common way of infecting a
system. It is not unheard of for an attacker to drop infected USB sticks in the parking lot and hope
someone will pick one up and plug it into the workstation.
Finally, these hardening activities can be supplemented by one more: regular reboot of the
workstation to protect against memory-only infections. Some of the more sophisticated attacks
involve installing memory resident malware that is hard to detect. Workstations that are targets
for this type of attack are those that run 24/7. Rebooting these workstations when time permits
will remove this type of malware.
Step 3: User account management
This involves managing user accounts. Users should be given only the privileges that they need,
and their passwords should be sufficiently long and require the use of a combination of three of
the following four: upper and lower case letters, numbers, and special characters. Granting a
limited set of privileges should reduce the ability of foreign software that has infected a user’s
program from using elevated privileges to perform some malicious act – a very common
technique used by malware.
Step 4: Security updates
Step 4 is making sure that security updates (patches) for both operating system and control
system software are kept up-to-date. These updates remove vulnerabilities that can be exploited
to infect the software containing the vulnerability. Free tools can be found on the Internet that
allow hackers to search a workstation for vulnerabilities and then automatically inject malicious
software that provides cmd.exe shell access to the workstation or that allows custom hacker code
to be downloaded to the workstation and run.
Of course, updates should be approved for the workstation so they do not disrupt workstation
software. Certified suppliers are required to validate all security patches for operation on their
systems.
Step 5: Backup and recovery
This involves implementing a backup and recovery plan. An effective backup and recovery plan
allows an infected system to have its configuration data and software restored to an uninfected
state. Certified suppliers are required to have a backup and recovery strategy that specifically
recommends when and how to recover a system to a stable state even if there is no evidence of
infection. This is important since sophisticated malware often hides itself from detection and can
sit dormant until the right time.
Step 6: Security monitoring and risk assessment
This involves monitoring the system for suspicious activity and performing risk assessments.
Security monitoring packages examine logs of workstations, firewalls, switches, and devices for
evidence of foreign software. Some monitoring packages inspect network traffic, as well as
processor and memory usage, looking for anomalies. In the absence of automated monitoring
packages, manual review of event and network traffic logs should be performed to look for
suspicious activity, such as an unexpected increase in network traffic, particularly at odd hours.
Risk assessments should be performed during initial design, prior to handover, and during the
maintenance cycle of the system to ensure that changes to the system have not been introduced
that weaken security. Actions taken after a risk assessment may include new firewall rules, new
switch ports to lockdown, stronger password policies, removal of unused software programs, and
better procedures for managing the connection of external devices like USB memory sticks.
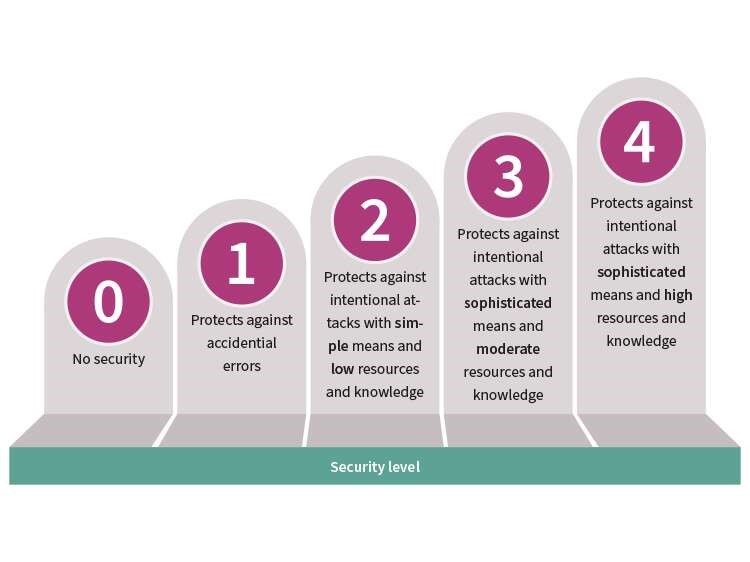
The IEC 62443 standard introduces the concept of security levels (SL) that can be applied to zones, conduits, channels, and products. The security level is defined by researching a particular device, and then determining what level of security it should have, depending on its place in the system.
- Level 1 is a casual exposure
- Level 2 is an intentional attack with low resources
- Level 3 is an intentional attack with moderate resources
- Level 4 is an intentional attack with extensive resources
The same concept of security levels (SL) is also applied to products. The IEC 62443-4-2 defines the security requirements for four types of components: software application requirements (SAR), embedded device requirements (EDR), host device requirements (HDR), and network device requirements (NDR).
Real-life strategies for strengthening PCS often stumble at the implementation stage. The initial step of auditing to identify vulnerabilities is clear, but moving to mitigation and ongoing monitoring proves challenging for many organizations. Common hurdles include complex technical solutions, limited resources, disruption concerns, and a gap in cybersecurity expertise.
A comprehensive managed program that is focused on both identifying vulnerabilities and building a robust defense mechanism is crucial to bridge this gap. Key components of such a program include:
- Develop a plan for maintenance and testing, then execute. Changes in complex systems are rarely plugand-play. Testing is necessary to maintain secure configurations and manage regular updates.
- Physical security. Combine cyber and physical security efforts to protect infrastructure. Monitor and control physical access.
- Documentation. Keep clear, easily accessible documentation for ongoing security management, including asset maintenance contacts.
- Policies and procedures. Develop, document, and communicate cybersecurity policies to ensure they are integrated into the organizational culture and practices. Clearly define cyber security roles, responsibilities, and authorities for managers, system administrators, and users.
- Education and training. Educate employees to ensure policies are widely understood and enforced. Vendor risk management. Evaluate and manage risks from third-party vendors and service providers.
- Simulation exercises. Conduct training exercises in a controlled environment to prepare for real incident recovery and enhance response capabilities. Establish PCS “Red Teams” to identify and evaluate possible attack scenarios
- Continuous monitoring. Provide ongoing support in managing cybersecurity measures that extends beyond the audit to include mitigation and proactive monitoring. Conduct physical security surveys and assess all remote sites connected to the PCS network to evaluate their security.
- Cybersecurity incident response planning. This is the preparation for any negative events that may affect the PCS and how to get back to normal as quickly as possible after the incident occurs. Its main elements include planning, incident prevention, detection, containment, remediation, recovery and restoration, and post incident analysis/forensics.
- Security of the supply chain and solution providers. Suppliers should provide security throughout the product lifecycle, including support, quality control, validation of performance, and vulnerability responses, among other aspects.
Conclusion:
The IEC 62443 standard brings together several important aspects widely discussed by a global community of subject matter experts (SME). It is difficult to simplify such an extensive body of information such as the IEC 62443. As a result, it is highly recommended that companies looking to adopt the recommendations of the IEC 62443 standard into their own applications consult certified partners and experts as they embark on their IEC 62443 journey.
Rules are developing. Several industries and suppliers use the basic IEC structure and add extra items.
Industrial security is more than just hardware and software. Project and support personnel have a
responsibility to promote security awareness at the site and to ensure that they are capable of
hardening a control system according to the security policies of the site.
As the development of IEC62443 standards and rules is an ongoing process, they must be frequently studied and assessed. In this document latest developments are incorporated; new developments will be added by means of new documents. Please check this site!
Used documents:
- 21 Steps to Improve Cyber Security of SCADA Networks: President’s Critical Infrastructure Protection Board. October 2001, Executive Order 13231.
- Cybersecurity Guidebook for Process Control. Emerson.
- NIST Cybersecurity Framework 2.0: RESOURCE & OVERVIEW GUIDE.
- SCADA cybersecurity: fortifying industrial control systems. Insights, APRIL 15, 2024
- Six Steps to Control System Cybersecurity. ISA.
Martin van Heun, senior process control engineer.


