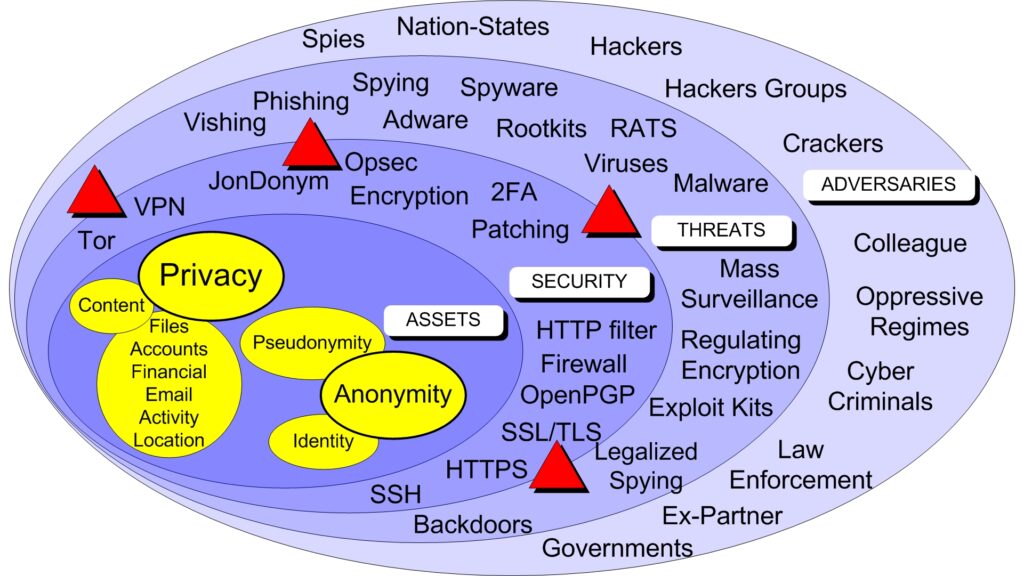
The cybersecurity landscape consists of:
- Assets: personal, software and hardware.
- Security: hardware and software.
- Threats: human, software and hardware.
- Adversaries: individuals, organisations, Nation-States and governmennts
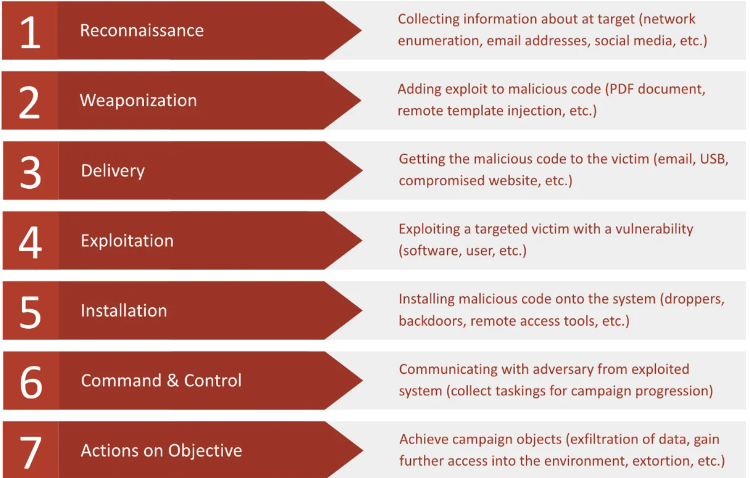
Hacking is a process and is described by means of The Lockheed Martin cybersecurity chain. This consists of:
The cyberattack effects consists of the following items:
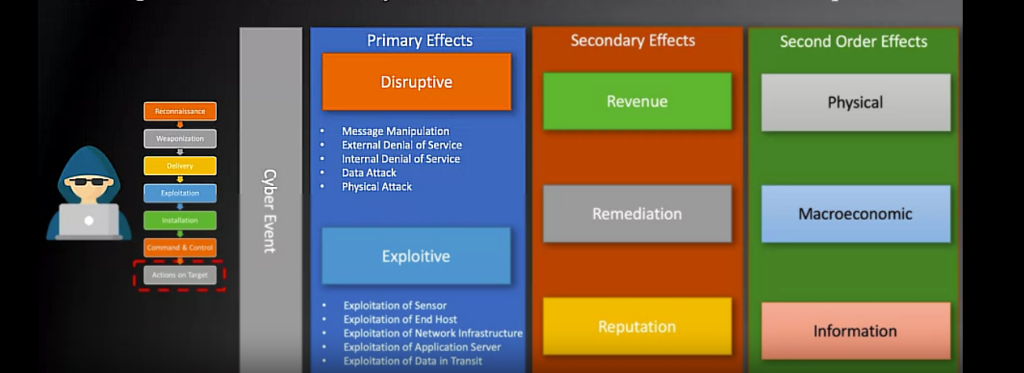
Primary effects have a direct impact on targeted devices.
Secundairy effects have an impact on organizational processes and capability: so on revenue, remediation and reputation.
Second order effects are the impacts on society: physical, macro-economic, informational/perception.